Facebook Metaverse Spark AR Hackathon Winners
 Skilling up is always encouraged at SRM University-AP. With cutting-edge technology and premier instructors provided to support curious, enthusiastic, and innovative minds, skilling up is fun, fantastic, and comes with fabulous prizes too.
Skilling up is always encouraged at SRM University-AP. With cutting-edge technology and premier instructors provided to support curious, enthusiastic, and innovative minds, skilling up is fun, fantastic, and comes with fabulous prizes too.
In the Metaverse Spark AR Hackathon conducted by Meta (Facebook), D Yogesh and Yash Agarwal have bagged the winner’s and runner’s up prizes of $300 and $200 respectively. Not just that, 154 of our students would take away from this competition lucrative goodies and participation certificates for their idea submissions.
The CR&CS department organized workshops and trained our students specifically for this event alongside their regular upskilling for placements and other hackathons and contests.
Over a huge number of students who participated in this contest from different corners of the globe, the students of SRMAP walking away with the prizes make a sizable chunk.
We extend our heartfelt wishes to all the participants and hope to see them ace every challenge they face with the knowledge imparted and the skills honed here.
Testimonials
“It was my first hackathon that I participated in and being a part of the SRM AP Hackathon Club has helped and motivated me greatly. Having an interest in AR/VR, this AR hackathon offered me a good opportunity to learn more about the technology. I attended a workshop, conducted by Meta where they introduced us to Augmented Reality. I learned how Instagram filters were made from scratch, and, in addition, I gained technical knowledge about Augmented Reality. I made an Instagram filter that was based on the PUBG Mobile game.
As part of the hackathon, I would like to thank the CR&CS department for the smooth conduction of the hackathon. Also, I would like to thank Priyanka ma’am (link here) and Raghunathan sir (link here) for their time and assistance in the process. I’m very happy that I have acquired a new skill and looking forward to contributing to the Metaverse! Explore the 4.0 technologies”
-Yogesh D
“The hackathon was about creating an AR effect. I made an AR effect on the theme based upon the popularly known web series “SQUID GAMES”.
A special thanks to one of my friends, S. Lokesh who helped me a lot to make me understand how to make an AR effect. I would like to thank Dr T. Raghunathan and Dr Priyanka from the SRM-AP Hackathon club for encouraging and guiding me to participate in this competition.
I am eagerly waiting for many more Hackathons wherein I can participate under the guidance of the SRM-AP hackathon club. Winning doesn’t matter, but participation matters”
-Yash Aggarwal
- Published in CSE NEWS, Departmental News, News, Students Achievements
Smart COVID-shield: An IoT driven reliable and automated prototype for Covid-19 symptoms tracking
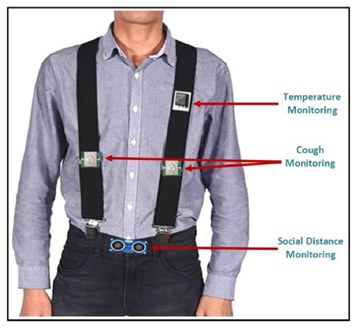
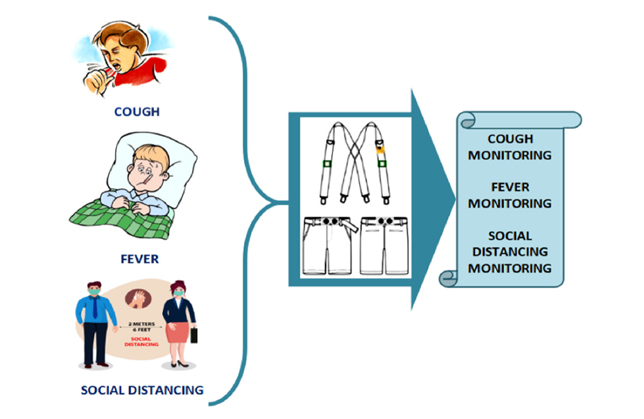 Persistent dry coughing and abnormally high body temperature are identified as more relevant risk factors associated with the COVID-19 crisis. Besides these, maintaining 6 feet social distancing norm was also recognized as a crucial factor. By taking these three features into consideration, the research group consisting of Dr Kshirasagar Sahoo, Assistant Professor, Department of Computer Science and Engineering at SRM University-AP have designed a smart, reliable and efficient COVID-19 tracking device model to monitor suspected infected people in public places. The device named “Smart COVID-Shield” utilising the IoT technology is equipped with a suspender and a belt to be placed over the clothes of the user which constitutes a cough detect unit, temperature detects unit and distance computing unit. Coughing and temperature patterns can be detected through the PIR sensor of the suspender while a belt with an ultrasonic sensor can be used to track people who violate the 6 feet social distancing norms in a real-time environment. A research paper titled “Smart COVID-shield: An IoT Driven Reliable and Automated Prototype for COVID-19 Symptoms Tracking” is published in Computing Journal as a part of the project.
Persistent dry coughing and abnormally high body temperature are identified as more relevant risk factors associated with the COVID-19 crisis. Besides these, maintaining 6 feet social distancing norm was also recognized as a crucial factor. By taking these three features into consideration, the research group consisting of Dr Kshirasagar Sahoo, Assistant Professor, Department of Computer Science and Engineering at SRM University-AP have designed a smart, reliable and efficient COVID-19 tracking device model to monitor suspected infected people in public places. The device named “Smart COVID-Shield” utilising the IoT technology is equipped with a suspender and a belt to be placed over the clothes of the user which constitutes a cough detect unit, temperature detects unit and distance computing unit. Coughing and temperature patterns can be detected through the PIR sensor of the suspender while a belt with an ultrasonic sensor can be used to track people who violate the 6 feet social distancing norms in a real-time environment. A research paper titled “Smart COVID-shield: An IoT Driven Reliable and Automated Prototype for COVID-19 Symptoms Tracking” is published in Computing Journal as a part of the project.
Abstract of the paper:
IoT technology is revolutionizing healthcare and is transforming it into more personalized healthcare. In the context of the COVID-19 pandemic, IoT’s intervention can help to detect its spread. This research proposes an effective “Smart COVID-Shield” that is capable of automatically detecting prevalent symptoms like fever and coughing along with ensuring social distancing norms are properly followed. It comprises three modules which include Cough Detect Module (CDM) for dry cough detection, Temperature Detect module (TDM) for high-temperature monitoring, and Distance Compute Module (DCM) to track social distancing norm violator. The device comprises a combination of a lightweight fabric suspender worn around the shoulders and a flexible belt wrapped around the waist. The suspender is equipped with a passive infrared (PIR) sensor and temperature sensor to monitor persistent coughing patterns and high body temperature and the ultra-sonic sensor verify 6 feet distance for tracking an individual’s social distancing norms. The developed model is implemented in an aluminium factory to verify its effectiveness. Results obtained were promising and reliable when compared to conventional manual procedures. The model accurately reported when body temperature rises. It outperformed thermal gun as it accurately recorded a mean of only 4.65 candidates with higher body temperature as compared to 8.59% with the thermal gun. A significant reduction of 3.61% on social distance violators was observed. Besides this, the latency delay of 10.32 s was manageable with a participant count of over 800 which makes it scalable.
This is a collaborative work of H. K. Tripathy, S. Mishra from School of Computer Engineering, KIIT Deemed to Be University, Bhubaneswar, Odisha, India and A. Nayyar from Graduate School, Faculty of Information Technology, Duy Tan University, Da Nang 550000, Vietnam.
Early detection of the coronavirus symptoms is one feasible means to restrict the spreading of coronavirus. The IoT enabled “Smart COVID-Shield” is developed and implemented in this study to monitor social distancing violators in crowded places. In future, all other COVID symptoms can be incorporated into the model to make it more effective and real-time. An emergency alert module can also be included as part of the model to create awareness among people. An enhanced security mechanism can be further embedded in the working model to prevent any data compromise and dilution in data availability.
- Published in CSE NEWS, News, Research News
Eco-friendly and economic production of Ammonia
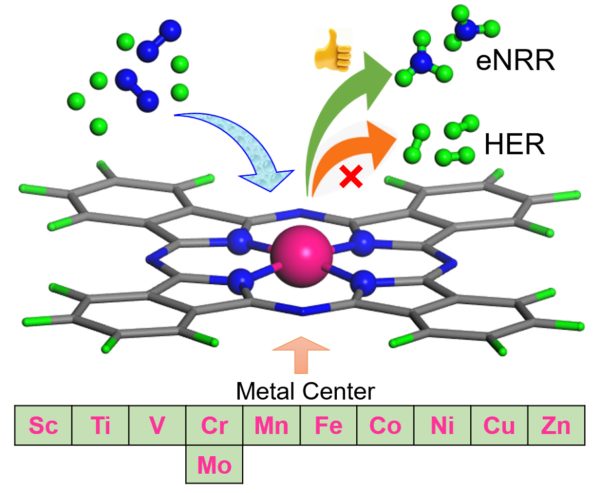 SRM Univeristy-AP is proud to announce that Prof. Ranjit Thapa, Department of Physics, has obtained a prestigious SERB-DST grant of Rs. 32 lakhs for a period of three years for his project, “Design Principle of Single Atom Catalyst for Nitrogen Fixation over HER: Energy Parameter, Electronic Descriptor and Database”.
SRM Univeristy-AP is proud to announce that Prof. Ranjit Thapa, Department of Physics, has obtained a prestigious SERB-DST grant of Rs. 32 lakhs for a period of three years for his project, “Design Principle of Single Atom Catalyst for Nitrogen Fixation over HER: Energy Parameter, Electronic Descriptor and Database”.
Ammonia (NH3) is the prime source of fertilizers and an important carrier of energy too. Ammonia can be stored in its chemical form for a long and it is easy to transport. So now researchers are looking forward to using ammonia in place of hydrogen as an energy source. But the production of ammonia with existing techniques needs more energy compared to the energy it stored in its chemical bond. So, an alternative process that is environmentally friendly and cost-effective is needed to be in place.
In 2019 the global production capacity of ammonia is 235 million metric tons and will increase to 290 million metric tons by 2030. The importance of ammonia is due to its application in broad and diverse fields, such as fertilizers, textiles, pharmaceuticals, and is a carbon-free energy carrier. The Haber-Bosch process is used for the synthesis of ammonia (NH3) from N2 and H2 using Fe based catalyst. But the process emits carbon dioxide (CO2) (1.5 tons of CO2/tons of NH3 production) requires high pressure and temperature and consumes around 2% of the global supply of energy. Electrocatalytic N2 fixation (N2 + 6H+ + 6e− → 2NH3) showed great potential due to the possible use of atmospheric nitrogen and hydrogen derived from water through electrolysis and in mild conditions. However, the slow kinetics of N2 adsorption, splitting of the strong N≡N bond are the challenges for the electrocatalytic NRR process. In the electrocatalytic NRR process, the fast reaction kinetics of hydrogen evolution reaction is the greatest obstacle. To solve these challenges, the search for various types of catalysts is on the roll.
To date, trial and error methods have been used to synthesize the catalysts for the electrocatalytic NRR process. Thanks to the rapid development of density functional theory-based computational methods, the intermediate steps during NRR can be identified at the atomic level, the underlying principles can be understood, and a large space of catalysts can be checked for efficient NRR within a limited time. Without understanding the correct electronic structure of SAC and its correlation with the overpotential of NRR and defining the correct energy parameter to define “NRR over HER” and “N2 binding over H binding free energy”, we can never design the best catalyst cost-effectively. We will address these problems through this project’s objectives.
The project will help to design the best single-atom catalyst for the reduction of nitrogen (from the air) through the electrocatalytic process and convert it into ammonia. The designed catalyst can be synthesis by the industry and can be used for NRR.
This project will help a step forward towards more ammonia production for the uses in the agriculture sector, energy sector, and related sector.
- Published in Departmental News, News, Physics News
Startup incubated by BBA student crosses ₹1 crore turnover
 Mr Lakshman Thatikonda, a 3rd year BBA student of SRM University-AP, has started his own business venture (TalentCrew), incubated at the Hatchlab Research Centre– The technology and livelihood business incubator of SRM University-AP.
Mr Lakshman Thatikonda, a 3rd year BBA student of SRM University-AP, has started his own business venture (TalentCrew), incubated at the Hatchlab Research Centre– The technology and livelihood business incubator of SRM University-AP.
The talent crew is a skill-based startup. They are one of India’s largest multi-category customised gifting companies, providing one of the best-curated collections of festival merchandise, gifts, handicrafts, wedding cards, carvings & personalised products for all occasions & festivals. TalentCrew has a global footprint with customers spanning 20 plus countries and the capability to deliver gifts to over 50 countries and 300 plus cities in India. Mr Lakshman started this organisation on the principles of creativity, agility, and social responsibility.
Over the next few years, TalentCrew envisions exploring and developing new products and services that will actively expand business while touching social responsibility.
Experience at Hatchlab Research Centre
The Hatchlab research centre aims to support SRM E-Cell’s mission of developing entrepreneurial talent and fostering the commercialisation of new ideas ventures. “Working with Hatchlab research centre was always a great experience. Here I found the fresh start for the innovation, and here the programme is very well structured with the right blend of practice,” says Mr Lakshman. “The best thing about this programme is that it allows me to learn while still being employed. And I always feel thankful for Dr Lakshmana Rao sir, for motivating me on every stand that I take, and Udayan Bakshi sir, for giving me such a wonderful opportunity” he added.
- Published in Blog, IDEA NEWS, Innovation, News, Paari Current Happenings, Students Achievements

