 In the last few years, due to the enormous development in communication technology, the sharing, and transmission of information have increased immensely. The information can be transferred in various forms, such as text, audio, video, and images. Mostly, the information or data is transmitted through open channels, which increases the possibility of illegal interception, fabrication, and modification of the original information. Thus, to avoid unauthorised access or alteration of data, the development of secure transmission systems is very important.
In the last few years, due to the enormous development in communication technology, the sharing, and transmission of information have increased immensely. The information can be transferred in various forms, such as text, audio, video, and images. Mostly, the information or data is transmitted through open channels, which increases the possibility of illegal interception, fabrication, and modification of the original information. Thus, to avoid unauthorised access or alteration of data, the development of secure transmission systems is very important.
The latest research from the Department of Physics evaluates the security strength of an improved optical cryptosystem based on interference. Assistant Prof Dr Ravi Kumar has published a paper, Security analysis on an interference-based optical image encryption scheme, in the Applied Optics journal, with an impact factor of 1.905.
Dr Ravi Kumar’s research is focused on the area of optical information processing and optical metrology. He studies and designs new optical cryptosystems with enhanced security features. For that, he uses various optical aspects and techniques, such as interference, diffractive imaging, polarization, computational imaging, etc. Alongside this, he also works in the area of digital holography and incoherent imaging. In this, he designs and develops new optical systems for imaging applications, such as super-resolution imaging, biomedical imaging, 3D imaging, telescopic applications, object detection, reconstruction, etc.
Explanation of the Research
Optical systems have been studied extensively for image encryption and found to be more reliable and efficient than their digital counterparts, such as parallel processing, capable of processing 2D data, multi-parameters capabilities (i.e., phase, wavelength, polarization, etc.), and can be employed as the security keys. The usage of biometric authentication in daily life, credit cards, fingerprint authentication, email/bank passwords, etc.; all need to be secured. This research can play an important role in designing a sophisticated cryptosystem for future technologies. Moreover, another direction of the research i.e., optical imaging, can be translated to design new low-cost biomedical devices (endoscopes, microscopes, biomedical sensors, etc.) which can have a significant social impact.
In the future, Dr Ravi Kumar will be focusing on the development of a new robust optical cryptosystem and designing new attack algorithms for existing optical encryption techniques. Additionally, he is also designing new optical imaging systems with better signal-to-noise ratios and improved resolution.
Abstract
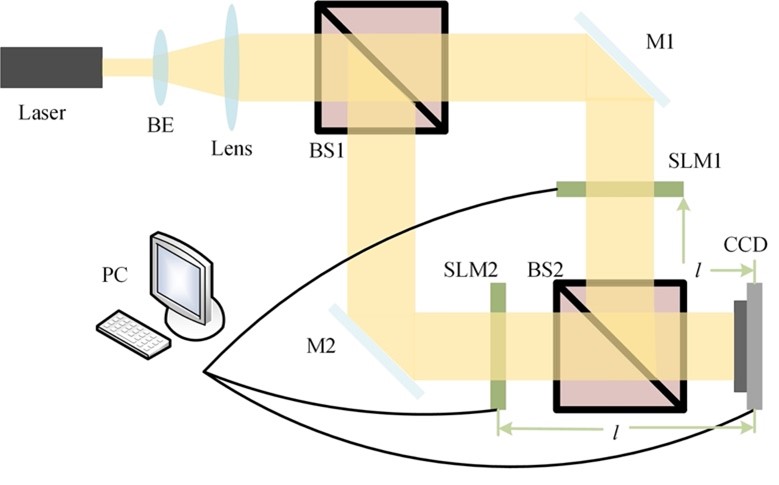
In this paper, the security strength of an improved optical cryptosystem based on interference has been evaluated. The plaintext was encoded into a phase-only mask (POM) and an amplitude mask (AM). Since the information of the plaintext cannot be recovered directly when one of the masks is released in the decryption process of an improved cryptosystem, it seems that it is free from the silhouette problem. However, researchers found that the random phase mask (RPM) that served as the encryption key is not related to the plaintext; thus, it is possible to recover the RPM firstly using the known-plaintext attack (KPA). Moreover, the POM and the AM generated in the encryption path only contains the phase and amplitude information, respectively; thus, these can be utilised as additional constraints in the proposed iterative process. Based on these findings, researchers have demonstrated two new kinds of hybrid attacks to crack the cryptosystem, i.e., a KPA and an iterative process with different constraints. To the best of our knowledge, it was the first time that the existence of a silhouette problem in the cryptosystem under study had been reported. Researchers have validated their attacks through numerical simulation.
Collaborations
Dr Xiong Yi, Jiangnan University, Wuxi 214122, China

