Smart devices and Internet of Things (IoT) are growing in importance every day and so do our security concerns about using them for our financial transactions. As we carry the world with us through wearable technology, Dr Sriramulu Bojjagani, Assistant Professor, Department of Computer Science Engineering works towards making wearable devices more secure.
With a thriving interest in Cyber Security, Formal Verification Methods and Vulnerability Analysis and Penetration Testing, Dr Bojjagani has recently published his paper on “A Secure IoT-based Micro-payment Protocol for Wearable Devices” in Peer-to-Peer Networking and Applications (PPNA), Springer.DOI: 10.1007/s12083-021-01242-y
Abstract:
Wearable devices are one of the parts of the essential cost of goods sold (COGS) in the wheel of the Internet of things (IoT), contributing towards a potential impact in the finance and banking sectors. There is a need for lightweight cryptography mechanisms for IoT devices because these are resource constraints. This paper introduces a novel approach to an IoT-based micro-payment protocol in a wearable device’s environment. This payment model uses “elliptic curve integrated encryption scheme (ECIES)” for encryption and decryption of the communicating messages between various entities. The proposed protocol allows the customer to buy the goods using a wearable device and send the mobile application’s confidential payment information. The application creates a secure session between the customer, banks, and merchant. The static security analysis and informal security methods indicate that the proposed protocol is withstanding the various security vulnerabilities involved in mobile payments. For logical verification of the correctness of security properties using the formal way of “Burrows-Abadi-Needham (BAN)” logic confirms the proposed protocol’s accuracy. The practical simulation and validation using the Scyther and Tamarin tool ensure the absence of security attacks in our scheme. Finally, the performance analysis based on cryptography features and computational overhead of related approaches specify that the proposed micro-payment protocol for wearable devices is secure and efficient.
Architecture for wearable devices:
The architecture for wearable devices is shown in Fig. 1. It consists of six types of entities, such as Issuer bank (IB), acquirer bank (AB), payment gateway (PG), a certification authority (CA), mobile terminal, and wearable sensing devices. The person using various wearable devices such as a smartwatch, smart wristband, smart glass, etc. In the architecture, a wearable device is connected to the mobile terminal through NFC. An app is running on a mobile device. Wearable devices are resource constraints because they have limited computing capabilities regarding battery, display, storage, and processing compared to a mobile terminal (smartphone). Hence, NFC is used to pair the wearable device and mobile terminal for transmitting public messages. Before conducting any transaction with the merchant, the customer and merchant should register their mobile numbers with the bank.
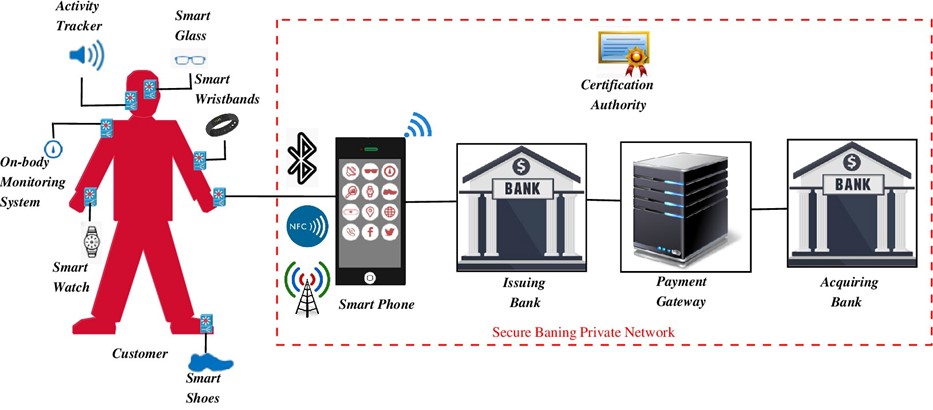
Fig. 1. Architecture for wearable devices
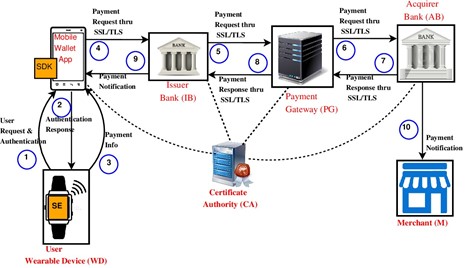
The customer can place an order with the merchant using the following steps and the complete messages flow in the proposed protocol is shown shown in the Figure.
● The customer places an order for an item through a wearable device.
● The request is transferred to the mobile app. The mobile app verifies the user authentication.
● After a successful authentication request, the app forwarded the request to the issuing bank for payment verification.
● The customer also sends a payment request for a deduction of the amount from his/her issuing bank.
● Once the bank validates the customer data in terms of sufficient funds available and user’s integrity. The issuing bank routes the transaction to the payment gateway through a secure network.
● In this step, the payment gateway verified the customer payment order and transferred it to the acquiring bank.
● If all the verifications are successful, then the transaction amount is then debited from the issuing bank and credited to the merchants’ acquiring bank.
Application demonstration:
As we know, most wearable devices run the Android operating system. The proposed framework developed as an Android application package (APK) file run in an Android wearable emulator, but we have operated in the Samsung Galaxy Note-2 device due to limits of the screen device and lack of environment. First, it needs to install the APK file and start running the app. Before running the app, some points need to be considered, such as the following:
● The company voice gateway provided for the service of an SMS gateway connected to Xeon server and assigned us a shortcode 56677.
● The payment gateway switch is used to communicate with the customer and merchant bank accounts.
● Two mobile numbers are registered with the banks and telecom operations, and it is used for SMS service.
● The deployed decryption web application on the Xeon server.
● HTTPS connection is used between voice gateway and Xeon server established Indian financial network (INFINET) link between server and bank.
We have not mentioned all the screenshots for the app from starting the login and authentication phase, but the protocol requires the essential information only shown in the screenshot. We didn’t mention the banks considered for implementing the micro-payment protocol for security and reputation reasons.
The proposed protocol action is as follows:
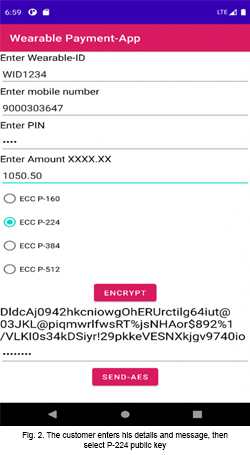
Step 1: The customer x runs a wearable application to enter Wearable-id, mobile number, pin and amount and sends an encrypted message to the Xeon server via short-code 56677. To encrypt the message, the customer may choose any one of the ECC curves as shown in Fig. 2.
Step 2: The SMS gateway receives the encrypted SMS, which is delivered to the server
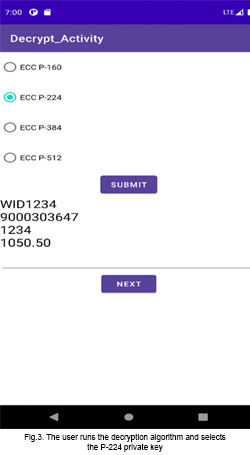
Step 3: The server receives the encrypted SMS and executes the decryption application. Next, the user runs decryption activity and selects the P-224 private key. After decryption, the message is shown in Fig. 3.
Step 4: After the message is decrypted, the user presses the “Next” button to communicate with the payment gateway.
Step 5: Now, the merchant fills in the remaining fields of merchant UPI-id, mobile number, and purpose of payment and then selects any payment gateway as shown in Fig. 4.
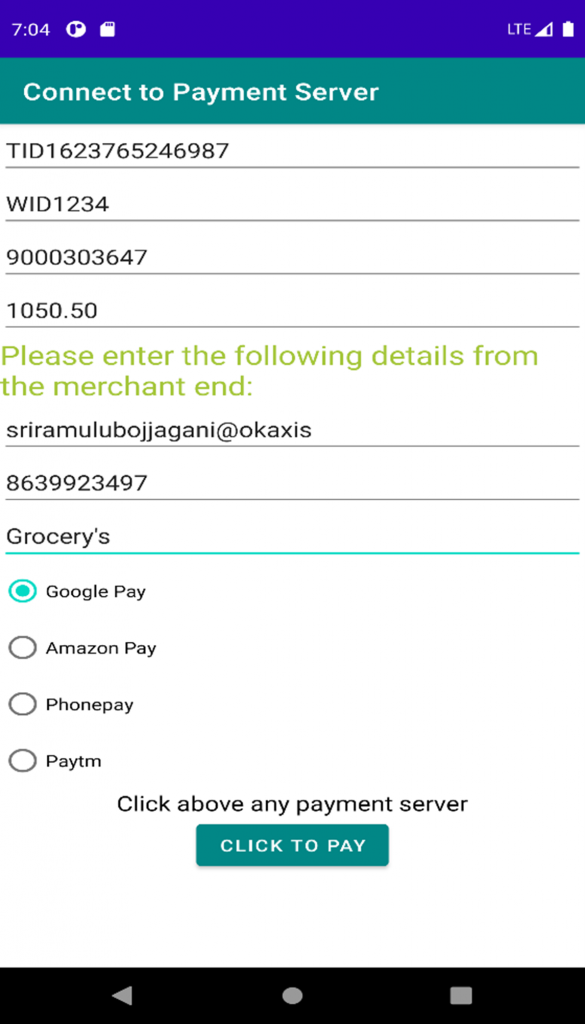
Fig. 4: The merchant enters the details and sends to any payment server
Dr Bojjagani’s research will further refine the parameters of security in IoT enabling wearable devices to become smarter and safer.
- To make the proposed protocols more secure can add biometric-based authentication can be added.
- The future directions of the proposed framework fit only for micro-payments. In future, we have upgraded to credit card/debit card payments to enhance the proposed framework for macro-payments.

