Recent News
- Ameliorated Follow the Leader: Algorithm and Application to Truss Design Problem June 9, 2022
Q1 journal publications of our faculty members always bring honour to SRM University-AP. Dr Priyanka Singh, Assistant Professor from the Department of Computer Science and Engineering has published a paper titled “Ameliorated Follow the Leader: Algorithm and Application to Truss Design Problem” in the journal Structures (Q1 journal) having an impact factor of 2.983.
Abstract
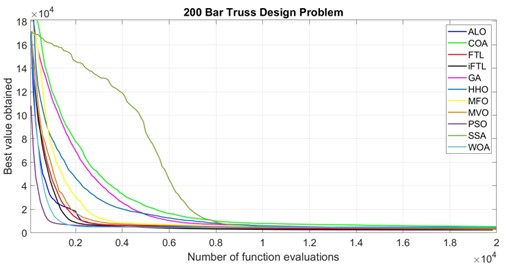 In the real world, resources, time, and money are always limited, necessitating the need for well-balanced algorithms. According to the “No-free-lunch” theorem, no single algorithm exists that works well in all applications. Hence, an optimisation algorithm with improved performance is always needed. The paper presents an improved follow the leader (iFTL) algorithm that imitates the behavioural movement of a sheep within the flock. The algorithm has been utilised to solve eight complex 10, 37, 52, 72, 120, 200, 224, and 942 bar truss design problems.
In the real world, resources, time, and money are always limited, necessitating the need for well-balanced algorithms. According to the “No-free-lunch” theorem, no single algorithm exists that works well in all applications. Hence, an optimisation algorithm with improved performance is always needed. The paper presents an improved follow the leader (iFTL) algorithm that imitates the behavioural movement of a sheep within the flock. The algorithm has been utilised to solve eight complex 10, 37, 52, 72, 120, 200, 224, and 942 bar truss design problems.Practical implications
The algorithm can be utilised to solve several structural and mechanical design problems such as bride design, antenna design, welded beam design, speed reducer, and many more. The algorithm is well suited for all types of real-life engineering problems where optimisation is required, from travel cost optimisation to optimisation of resources in the organisation under the given constraints and objective function.
Collaborators
1. Rahul Kottath (Computer Vision Engineer, Digital Tower, Bentley Systems India Private Limited, Pune, India)
2. Ghanshyam G. Tejani (Assistant Professor, Department of Mechanical Engineering, School of Technology, GSFC University, Vadodara, Gujarat, India)Future Research Plan
Currently, Dr Priyanka is exploring new engineering applications where optimisation techniques can be used. She is working on optimisation methods that can be utilised to classify microarray data, energy optimisation, and mechanical and structural design problems. In future, she plans to propose her work to the industrial level for the greater good and better solutions.
Continue reading → - Computing Influential nodes in complex networks June 7, 2022
With its vast applications in the industry, computing influential nodes is becoming a popular research field in recent days. The Department of Computer Science and Engineering is delighted to inform you that the paper, Computing Influential Nodes Using Nearest Neighborhood Trust Value and Pagerank in Complex Networks have been published by Dr Murali Krishna Enduri, Assistant Professor, Dr Satish Anamalamudi, Associate Professor, and the PhD students; Koduru Hazarathaiah, Ms Srilatha Tokala in the Entropy Journal (Q2 Journal), with an impact factor 2.587.
Abstract
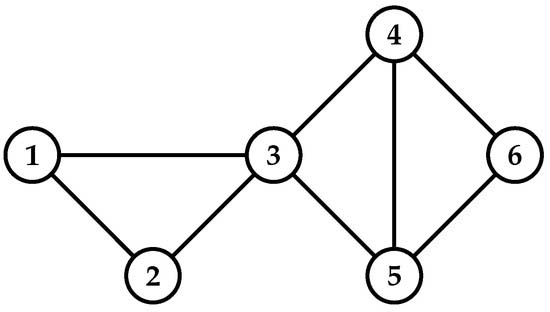 Computing influential nodes attract many researchers’ attention for spreading information in complex networks. It has vast applications such as viral marketing, social leaders, rumour control, and opinion monitoring. The information spreading ability of influential nodes is more compared with other nodes in the network. Several researchers proposed centrality measures to compute the influential nodes in the complex network, such as degree, betweenness, closeness, semi-local centralities, PageRank, etc. These centrality methods are defined based on the local and/or global information of nodes in the network. However, due to the high time complexity, centrality measures based on the global information of nodes have become unsuitable for large-scale networks. Very few centrality measures exist that are based on the attributes between nodes and the structure of the network. We propose the Nearest Neighbourhood Trust PageRank (NTPR) based on the structural attributes of neighbours and nearest neighbours of nodes. We define the measure based on the degree ratio, the similarity between nodes, the trust value of neighbours, and the nearest neighbours.
Computing influential nodes attract many researchers’ attention for spreading information in complex networks. It has vast applications such as viral marketing, social leaders, rumour control, and opinion monitoring. The information spreading ability of influential nodes is more compared with other nodes in the network. Several researchers proposed centrality measures to compute the influential nodes in the complex network, such as degree, betweenness, closeness, semi-local centralities, PageRank, etc. These centrality methods are defined based on the local and/or global information of nodes in the network. However, due to the high time complexity, centrality measures based on the global information of nodes have become unsuitable for large-scale networks. Very few centrality measures exist that are based on the attributes between nodes and the structure of the network. We propose the Nearest Neighbourhood Trust PageRank (NTPR) based on the structural attributes of neighbours and nearest neighbours of nodes. We define the measure based on the degree ratio, the similarity between nodes, the trust value of neighbours, and the nearest neighbours.Explanation of the research
The research computes the influential nodes on the various real-world networks by using the proposed centrality method NTPR. The researchers find the maximum influence by using influential nodes with SIR and independent cascade methods. They also compare the maximum influence of our centrality measure with the existing basic centrality measures.
Social implications
Viral Marketing is a business strategy that uses existing social networks to promote products. The influential nodes in complex networks can be found using the centrality measure and can be used as the seed nodes for promoting products in the social networks. A rumour is a statement being said without knowing if it is true or not. The rumours can be easily controlled by discovering influential nodes. The researchers look forward to finding a centrality measure to detect the influential nodes efficiently.
Continue reading →

