Recent News
- SLP-E: Enhancing Privacy and Lifespan in WSNs for IoT December 13, 2023
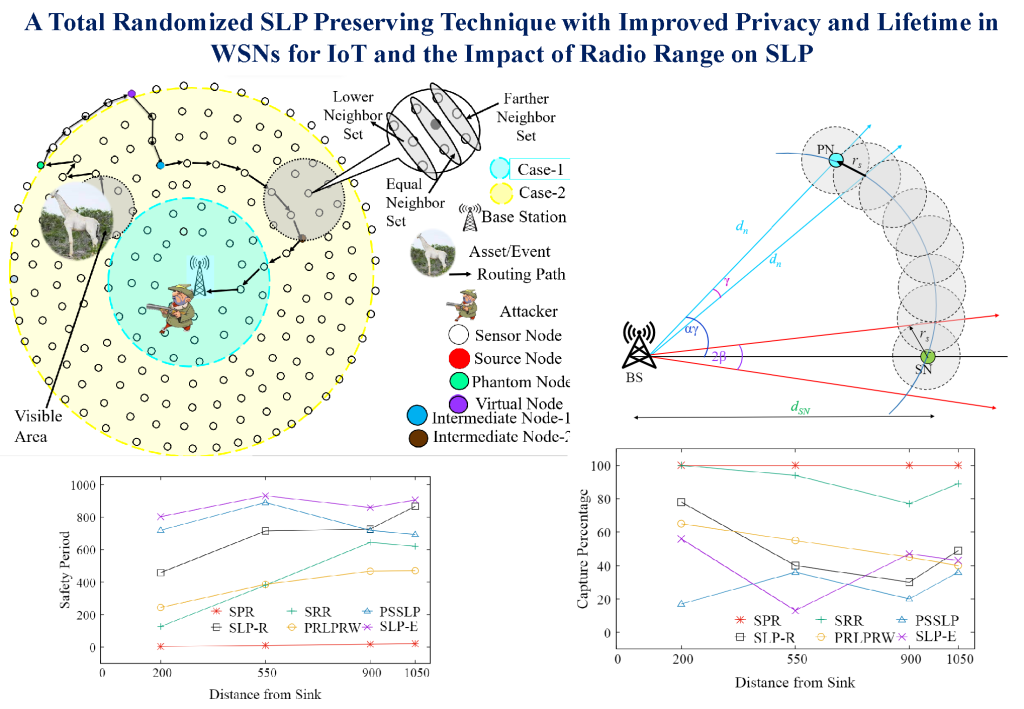
The Department of Computer Science and Engineering is thrilled to share that the paper titled, “A Total Randomized SLP Preserving Technique with Improved Privacy and Lifetime in WSNs for IoT and the Impact of Radio Range on SLP” has been published by Dr Manjula R, Assistant Professor, Department of CSE, and BTech-CSE Student Mr Tejodbhav Koduru in “Sensors“, a Q2 journal, having an Impact Factor of 3.9. Their research addresses the critical need for improved source location privacy and extended network longevity, presenting a pioneering solution known as Source Location Privacy with Enhanced Privacy and Network Lifetime (SLP-E).
Abstract
SLP-E utilises a unique combination of techniques, including a reverse random walk, a walk on annular rings, and min-hop routing, to diversify routing pathways within the network. Unlike existing SLP techniques that either prioritize privacy over network lifetime or vice versa, this approach aims to simultaneously enhance safety period, network lifetime, and privacy uniformly. Notably, this research also explores the impact of sensor radio range on Network Lifetime metrics and privacy strength within the context of SLP in WSN.
Practical Implementation/Social Implications of the research
This research holds real-world significance, especially in scenarios like protecting a lone white giraffe in Kenya fitted with a GPS tracker. Poachers pose a serious threat to such animals, hacking GPS devices to locate and harm them. This solution offers a viable approach to mitigate these threats, providing practical implications for the conservation of endangered species.
Collaborations
- Mr Tejodbhav Koduru from SRM University-AP
- Prof. Raja Datta from IIT Kharagpur
- Ms Florence Mukamanzi, Dr Damien Hanyurwimfura and Prof. Mukanyiligira Didacienne from the African Center of Excellence in the Internet of Things, University of Rwanda
- Teacher-Student Duo Author a Chapter on Graph Neural Networks August 28, 2023

Dr Ravi Kant Kumar, Assistant Professor at the Department of Computer Science and Engineering at SRM University-AP and his research scholar, Ms Gayathri Dhara have recently made a significant contribution to the field of Graph Neural Networks. The teacher-student duo have offered relevant analysis of visual saliency applications using Graph Neural Networks (GNN) in their book chapter titled “Study and Analysis of Visual Saliency Applications Using Graph Neural Networks” in the book, Concepts and Techniques of Graph Neural Networks. The topic of their study will prove to be a key source of reference for industry professionals, researchers, scholars, academicians, practitioners, instructors, and students.
Description and Significance of the Chapter
The chapter covers the practical applications of GNN in the field of visual saliency. Various applications of computer vision problems implemented using graph neural networks (GNNs) have been studied and analysed in this chapter. It also includes the design approach of GNN, the various computational models used in GNN, its challenges and recommendations. The social significance of GNN in visual saliency extends to various domains like Human attention modelling, Advertising and marketing, Visual content understanding, and so on.
Significance of GNNs
Graph Neural Networks (GNNs) have gained significance in the field of visual saliency due to their ability to model complex relationships and dependencies within visual data. Visual saliency refers to the process of predicting the most visually prominent regions or areas in an image or video that attract human attention. It plays a crucial role in various computer vision applications, such as image understanding, object recognition, and scene understanding. GNNs can learn spatial dependencies and feature representations from visual data. There are many methodologies that address the detection of the salient object using GNN. GNNs can handle multi-modal data, combining visual information with other modalities such as textual or semantic features. This integration allows GNNs to leverage additional cues and contextual information to improve visual saliency prediction. So, studying these different salient object detection methods using GNN and knowing the challenges of GNN will help in meeting our research objectives.
Continue reading →

