Wireless Sensor Networks (WSNs) and their derivatives such as Internet of Things (IoT) and the Internet of Industrial Things (IIOT) are no longer confined to traditional applications such as smart homes and transportation. It has already marked its presence in Industrial applications and extended even to wildlife conservation. The impending concerns associated with such wireless networks are their privacy and security. One such menace afflicting wildlife is cyber poaching. Taking this into consideration, Dr Manjula R, Assistant Professor, and her student Mr Tejodbhav Koduru, from the Department of Computer Science and Engineering, have published a paper, “Position-independent and Section-based Source Location Privacy Protection in WSN” in the journal, ‘IEEE Transactions on Industrial Informatics’ having an Impact Factor of 10.215. The article is published in collaboration with Ms Florence Mukamanzi from the University of Rwanda, Rwanda, Africa and Prof Raja Datta from IIT Kharagpur, West Bengal, India.
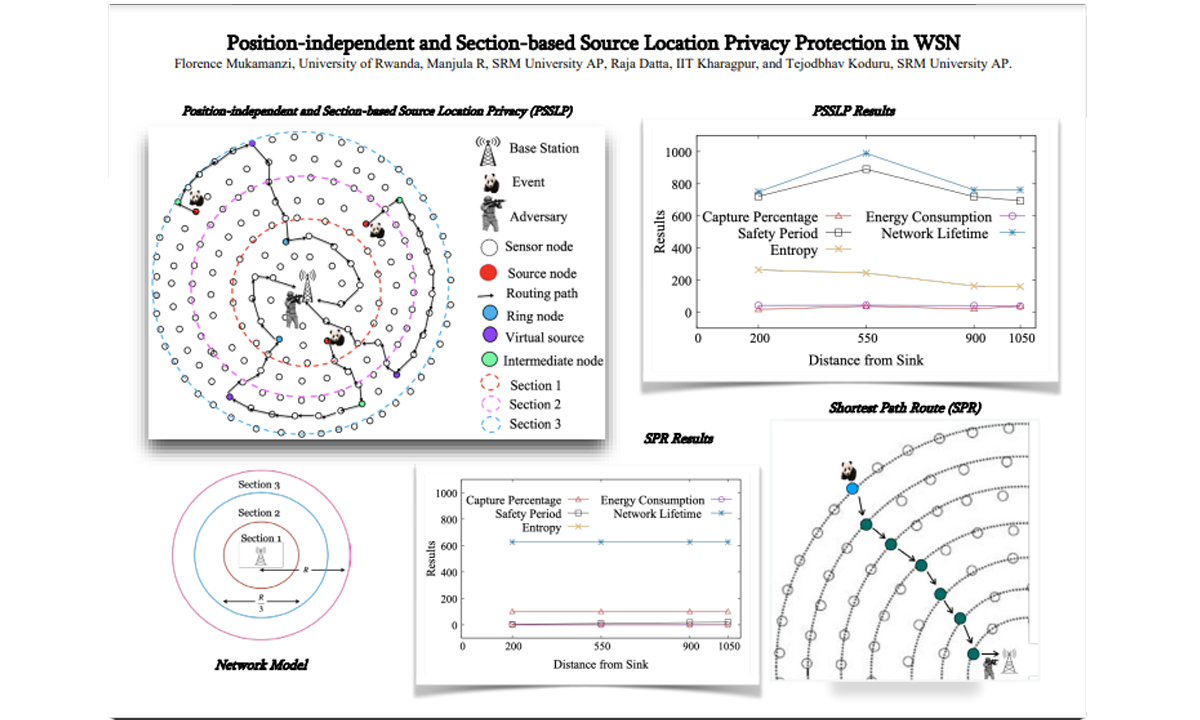
The sensors collect data about these endangered animals and report it to the central controller which is connected to the Internet. Over the period, the hunters have also evolved and are equipped with smart devices that help them to easily locate the animal with minimal effort. In the simplest form, the attacker or the hunter just eavesdrops on the communication links to know the message’s origin and backtrack to the source of information. Once the source of information i.e., the location is identified then the endangered animal is captured. To overcome such backtracking issues, their work aims at delaying the information disclosure to the attacker through traffic obfuscation.
Although it may not act as an ultimate solution, the research work focuses on contextual privacy, unlike traditional content privacy. The attacker collects only contextual information such as packet rate, traffic intensities, routing paths, time correlations etc., to determine the source of information. The work focuses on mitigating traffic correlation i.e., hop-by-hop backtrack attacks and protecting the assets that are monitored using WSNs. The performance metrics include safety period and network lifetime amongst other metrics. The proposed random-walk-based routing solution achieves an improved safety period and network lifetime compared to the existing schemes. The work was simulated using a custom-designed simulation tool and was validated with the numerical results obtained using mathematical models.
The proposed solutions could be seamlessly used in monitoring endangered animals such as rhinoceros or in military applications to track soldiers. In addition, the routing algorithm could also be used in delaying tolerant networks to improve the efficiency and lifetime of the network, in designing the random trajectories of bio-nano bots for intrabody monitoring etc. Their future research plan includes developing improved source location privacy preservation techniques for terrestrial and underwater wireless sensor networks using the benefits of Artificial Intelligence and Machine Learning. In addition, they also aims at the development of data collection and routing protocols for intrabody nanonetwork operating at tera hertz frequencies— next-generation networks, envisioned networks.